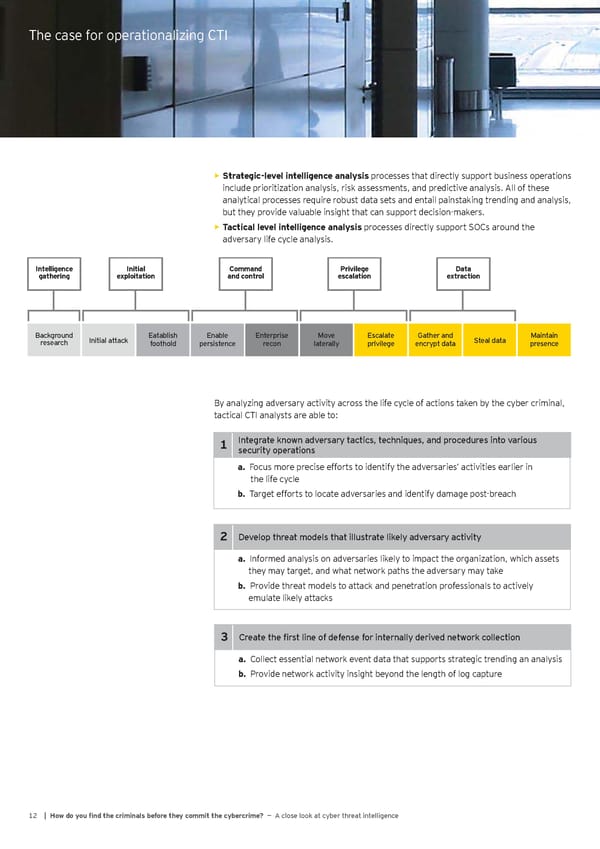
The case for operationalizing CTI Strategic%level intelligence analysis processes that directly support business operations • include prioritization analysis, risk assessments, and predictive analysis. All of these analytical processes require robust data sets and entail painstaking trending and analysis, but they provide valuable insight that can support decision-makers. Tactical level intelligence analysis processes directly support SOCs around the • adversary life cycle analysis. Intelligence Initial Command Privilege Data gathering exploitation and control escalation extraction Background Initial attack Eatablish Enable Enterprise Move Escalate Gather and Steal data Maintain research foothold persistence recon laterally privilege encrypt data presence By analyzing adversary activity across the life cycle of actions taken by the cyber criminal, tactical CTI analysts are able to: 1 Integrate known adversary tactics, techniques, and procedures into various security operations a& Focus more precise efforts to identify the adversaries’ activities earlier in the life cycle b& Target efforts to locate adversaries and identify damage post-breach 2 Develop threat models that illustrate likely adversary activity a& Informed analysis on adversaries likely to impact the organization, which assets they may target, and what network paths the adversary may take b& Provide threat models to attack and penetration professionals to actively emulate likely attacks 3 Create the first line of defense for internally derived network collection a& Collect essential network event data that supports strategic trending an analysis b& Provide network activity insight beyond the length of log capture 12 | @ow do you Ônd the criminals before they commit the cybercrime? — A close look at cyber threat intelligence
 Cyber Threat Intelligence Report Page 13 Page 15
Cyber Threat Intelligence Report Page 13 Page 15