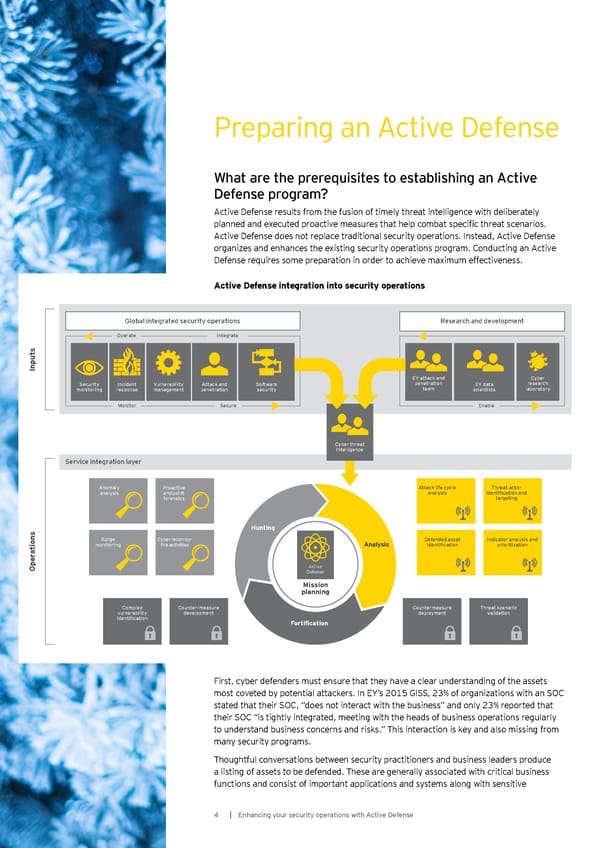
P reparing an A ctive D ef ense What are the prerequisites to establishing an Active Def ense program? A ctive D ef ense resu lts f rom the f u sion of timely threat intelligence w ith delib erately planned and executed proactive measures that help combat specific threat scenarios. A ctive D ef ense does not replace traditional secu rity operations. Instead, A ctive D ef ense organizes and enhances the existing security operations program. Conducting an Active D ef ense req u ires some preparation in order to achieve max imu m ef f ectiveness. A ctiv e D efense integration into security op erations Global integrated security operations Research and development O perate Integrate s t u p n I E Y attack and C y ber S ecu rity Incident Vulnerability A ttack and S of tw are penetration E Y data research monitoring response management penetration secu rity team scientists laboratory M onitor S ecu re Enable C y ber threat intelligence Service integration layer Anomaly P roactive Attack life cycle T hreat actor analysis endpoint analysis identification and f orensics targeting s H unting n S u rge C y ber recon- by - Def ended asset Indicator analysis and o monitoring fire activities A nal ysis identification prioritiz ation ti ra e p A ctive O D ef ense M ission p l anning Complex C ou nter- measu re C ou ntermeasu re T hreat scenario vulnerability development deployment validation identification Fortification First, cyber defenders must ensure that they have a clear understanding of the assets most coveted by potential attackers. In EY’s 2015 GISS, 23% of organizations with an SOC stated that their S O C , “ does not interact w ith the b u siness” and only 2 3 % reported that their S O C “ is tightly integrated, meeting w ith the heads of b u siness operations regu larly to understand business concerns and risks.” This interaction is key and also missing from many secu rity programs. Thoughtful conversations between security practitioners and business leaders produce a listing of assets to be defended. These are generally associated with critical business f u nctions and consist of important applications and sy stems along w ith sensitive 4 | E nhancing y ou r secu rity operations w ith A ctive Def ense
 Enhancing your Security Operations with Active Defense Page 5 Page 7
Enhancing your Security Operations with Active Defense Page 5 Page 7