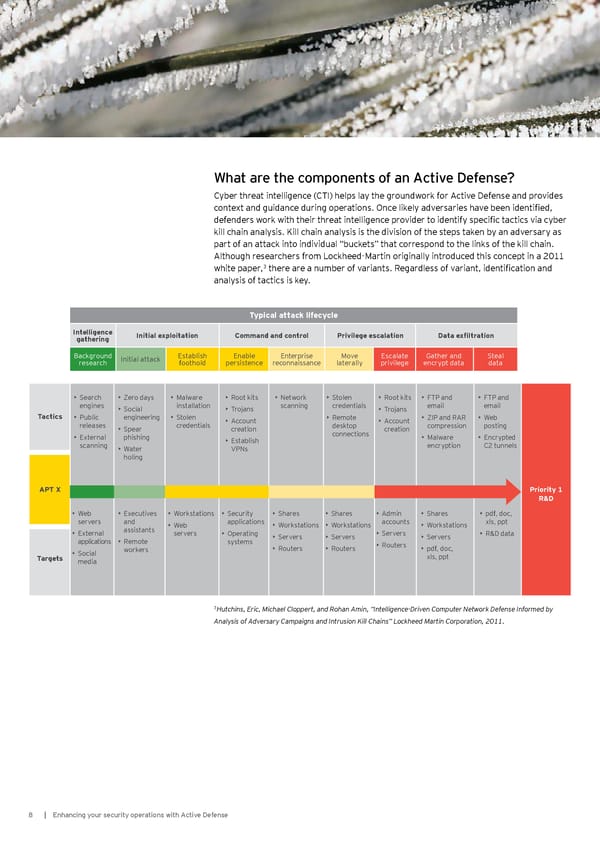
W hat are the components of an A ctive Def ense? Cyber threat intelligence (CTI) helps lay the groundwork for Active Defense and provides context and guidance during operations. Once likely adversaries have been identified, defenders work with their threat intelligence provider to identify specific tactics via cyber kill chain analy sis. K ill chain analy sis is the division of the steps taken b y an adversary as part of an attack into individu al “ b u ckets” that correspond to the links of the kill chain. A lthou gh researchers f rom L ockheed- M artin originally introdu ced this concept in a 2 0 1 1 w hite paper,3 there are a number of variants. Regardless of variant, identification and analy sis of tactics is key . Typ ical attack l ifecycl e Intel l igence Initial ex p l oitation Com m and and control P riv il ege escal ation Data exfiltration gathering B ackgrou nd Initial attack Establish Enable Enterprise M ove Escalate Gather and S teal research f oothold persistence reconnaissance laterally privilege encry pt data data • S earch • Z ero day s • M alw are • R oot kits • N etw ork • S tolen • R oot kits • FTP and • FTP and engines • S ocial installation • Trojans scanning credentials • Trojans email email Tactics • P u b lic engineering • S tolen • A ccou nt • R emote • A ccou nt • Z IP and R A R • W eb releases • S pear credentials creation desktop creation compression posting • External phishing connections • M alw are • Encrypted scanning • Establish encry ption C 2 tu nnels • W ater V P N s holing A P T X P riority 1 R & D • W eb • Executives • W orkstations • S ecu rity • S hares • S hares • A dmin • S hares • pdf , doc, servers and • W eb applications • W orkstations • W orkstations accou nts • W orkstations x ls, ppt • External assistants servers • O perating • S ervers • R & D data applications • R emote sy stems • S ervers • S ervers • S ervers w orkers • R ou ters • R ou ters • R ou ters • pdf , doc, Targets • S ocial x ls, ppt media 3 Hutchins, Eric, Michael Cloppert, and Rohan Amin, “Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains” Lockheed Martin Corporation, 2011. 8 | E nhancing y ou r secu rity operations w ith A ctive Def ense
 Enhancing your Security Operations with Active Defense Page 9 Page 11
Enhancing your Security Operations with Active Defense Page 9 Page 11