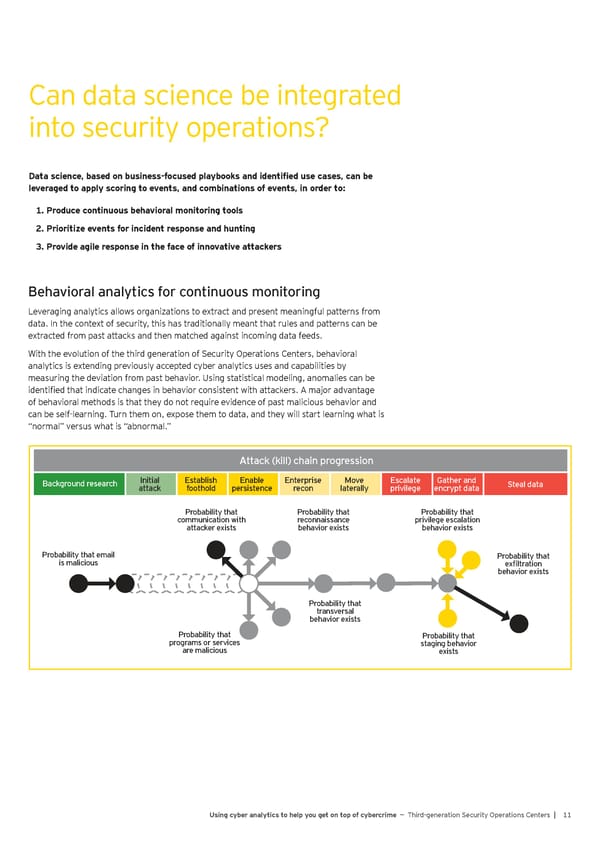
Can data science be integrated into security operations? Data science, based on business-focused playbooks and identified use cases, can be leveraged to apply scoring to events, and combinations of events, in order to: 1. Produce continuous behavioral monitoring tools 2. Prioritize events for incident response and hunting 3. Provide agile response in the face of innovative attackers Behavioral analytics for continuous monitoring Leveraging analytics allows organizations to extract and present meaningful patterns from data. In the context of security, this has traditionally meant that rules and patterns can be extracted from past attacks and then matched against incoming data feeds. With the evolution of the third generation of Security Operations Centers, behavioral analytics is extending previously accepted cyber analytics uses and capabilities by measuring the deviation from past behavior. Using statistical modeling, anomalies can be identified that indicate changes in behavior consistent with attackers. A major advantage of behavioral methods is that they do not require evidence of past malicious behavior and can be self-learning. Turn them on, expose them to data, and they will start learning what is “normal” versus what is “abnormal.” Attack (kill) chain progression Attack (kill) chain progression Background research Initial Establish Enable Enterprise Move Escalate Gather and Steal data attack foothold persistence recon laterally privilege encrypt data Probability that Probability that Probability that communication with reconnaissance privilege escalation attacker exists behavior exists behavior exists Probability that email Probability that is malicious exfiltration behavior exists Probability that transversal behavior exists Probability that Probability that programs or services staging behavior are malicious exists Using cyber analytics to help you get on top of cybercrime — Third-generation Security Operations Centers | 11
 Using Cyber Analytics to help you get on top of Cybercrime Page 12 Page 14
Using Cyber Analytics to help you get on top of Cybercrime Page 12 Page 14