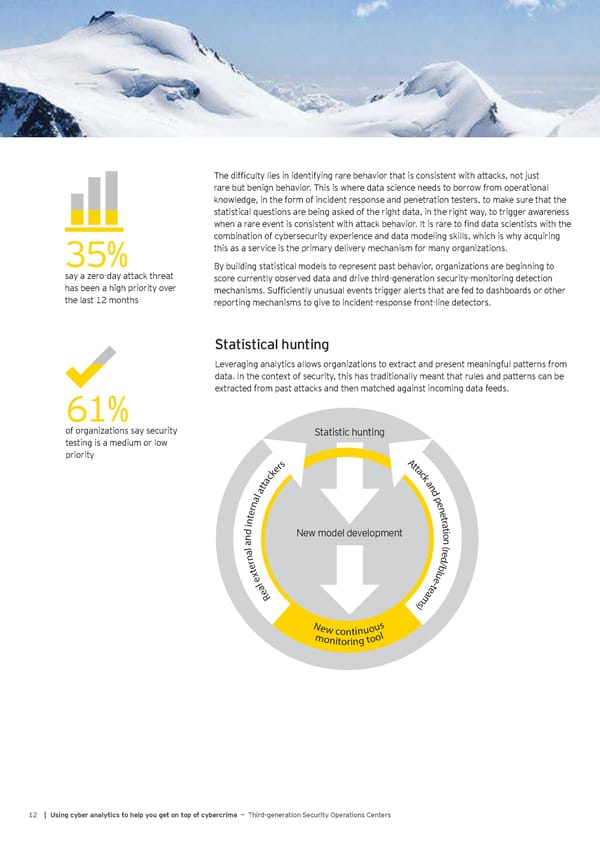
The difficulty lies in identifying rare behavior that is consistent with attacks, not just rare but benign behavior. This is where data science needs to borrow from operational knowledge, in the form of incident response and penetration testers, to make sure that the statistical questions are being asked of the right data, in the right way, to trigger awareness when a rare event is consistent with attack behavior. It is rare to find data scientists with the combination of cybersecurity experience and data modeling skills, which is why acquiring 35% this as a service is the primary delivery mechanism for many organizations. 70%@40 transparency By building statistical models to represent past behavior, organizations are beginning to say a zero-day attack threat score currently observed data and drive third-generation security-monitoring detection has been a high priority over mechanisms. Sufficiently unusual events trigger alerts that are fed to dashboards or other the last 12 months reporting mechanisms to give to incident-response front-line detectors. 62% Statistical hunting 61% Leveraging analytics allows organizations to extract and present meaningful patterns from data. In the context of security, this has traditionally meant that rules and patterns can be 61% extracted from past attacks and then matched against incoming data feeds. 54% of organizations say security Statistic hunting testing is a medium or low priority A s t r t e a k c c k a a t n t d a l p a e n n r e e t t r n a i t d New model development ion n a la er( nre b/d txe eul la et- eR ma )s New continuous monitoring tool 12 | Using cyber analytics to help you get on top of cybercrime — Third-generation Security Operations Centers
 Using Cyber Analytics to help you get on top of Cybercrime Page 13 Page 15
Using Cyber Analytics to help you get on top of Cybercrime Page 13 Page 15