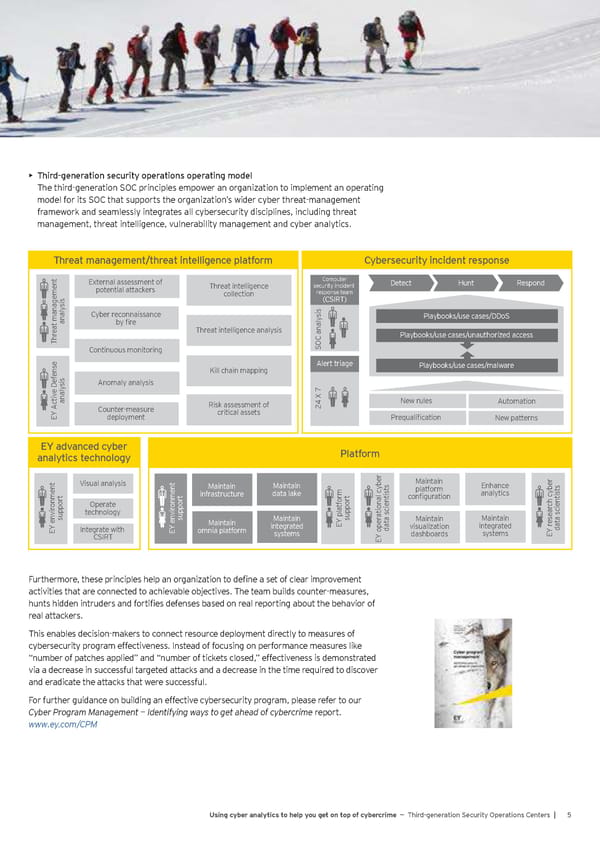
• Third-generation security operations operating model The third-generation SOC principles empower an organization to implement an operating model for its SOC that supports the organization’s wider cyber threat-management framework and seamlessly integrates all cybersecurity disciplines, including threat management, threat intelligence, vulnerability management and cyber analytics. Third-generation Security Operations Operating Model Threat management/threat intelligence platform Cybersecurity incident response t External assessment of Computer Detect Hunt Respond potential attackers Threat intelligence security incident collection response team sis (CSIRT) analy Cyber reconnaissance sis Playbooks/use cases/DDoS at managemen by fire e Threat intelligence analysis Playbooks/use cases/unauthorized access hr T SOC analy Continuous monitoring e Alert triage Playbooks/use cases/malware ens Kill chain mapping f sis Anomaly analysis e De analy Risk assessment of 24 X 7 New rules Automation Y Activ Counter-measure critical assets E deployment Prequalification New patterns EY advanced cyber Platform analytics technology t Visual analysis t Maintain Maintain yber s Maintain Enhance s infrastructure data lake t platform analytics ybert t t ormt tis configuration tis onmen Operate onmen f cien ch ccien vir technology vir ar ational c e suppor suppor Maintain Y platsuppor a s Maintain Maintain s a s Y en Y en Maintain integrated E dat visualization integrated e dat E Integrate with E omnia platform systems dashboards systems Y r CSIRT Y oper E E Furthermore, these principles help an organization to define a set of clear improvement activities that are connected to achievable objectives. The team builds counter-measures, hunts hidden intruders and fortifies defenses based on real reporting about the behavior of real attackers. This enables decision-makers to connect resource deployment directly to measures of cybersecurity program effectiveness. Instead of focusing on performance measures like “number of patches applied” and “number of tickets closed,” effectiveness is demonstrated via a decrease in successful targeted attacks and a decrease in the time required to discover and eradicate the attacks that were successful. For further guidance on building an effective cybersecurity program, please refer to our Cyber Program Management — Identifying ways to get ahead of cybercrime report. www.ey.com/CPM Using cyber analytics to help you get on top of cybercrime — Third-generation Security Operations Centers | 5
 Using Cyber Analytics to help you get on top of Cybercrime Page 6 Page 8
Using Cyber Analytics to help you get on top of Cybercrime Page 6 Page 8