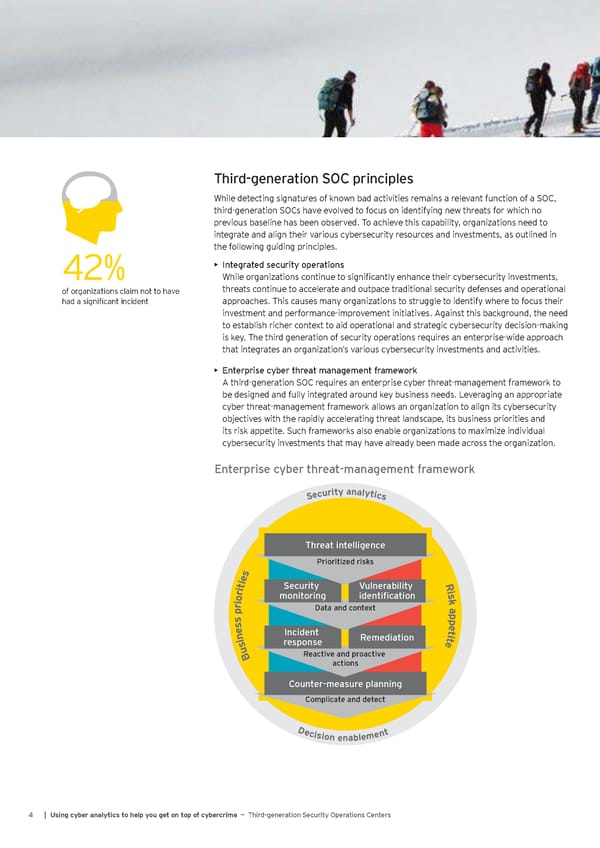
Third-generation SOC principles While detecting signatures of known bad activities remains a relevant function of a SOC, third-generation SOCs have evolved to focus on identifying new threats for which no previous baseline has been observed. To achieve this capability, organizations need to integrate and align their various cybersecurity resources and investments, as outlined in the following guiding principles. 42% • Integrated security operations While organizations continue to significantly enhance their cybersecurity investments, of organizations claim not to have threats continue to accelerate and outpace traditional security defenses and operational had a significant incident approaches. This causes many organizations to struggle to identify where to focus their investment and performance-improvement initiatives. Against this background, the need to establish richer context to aid operational and strategic cybersecurity decision-making is key. The third generation of security operations requires an enterprise-wide approach that integrates an organization’s various cybersecurity investments and activities. • Enterprise cyber threat management framework A third-generation SOC requires an enterprise cyber threat-management framework to be designed and fully integrated around key business needs. Leveraging an appropriate cyber threat-management framework allows an organization to align its cybersecurity objectives with the rapidly accelerating threat landscape, its business priorities and its risk appetite. Such frameworks also enable organizations to maximize individual cybersecurity investments that may have already been made across the organization. Enterprise cyber threat management framework Enterprise cyber threat-management framework a n y t a i l r y u t c i e c S s Threat intelligence Prioritized risks s e R i Security Vulnerability t i i r monitoring identification s o k i r Data and context a p p sse tep ni Incident Remediation eti su response B Reactive and proactive actions Counter-measure planning Complicate and detect Decision enablement 4 | Using cyber analytics to help you get on top of cybercrime — Third-generation Security Operations Centers
 Using Cyber Analytics to help you get on top of Cybercrime Page 5 Page 7
Using Cyber Analytics to help you get on top of Cybercrime Page 5 Page 7