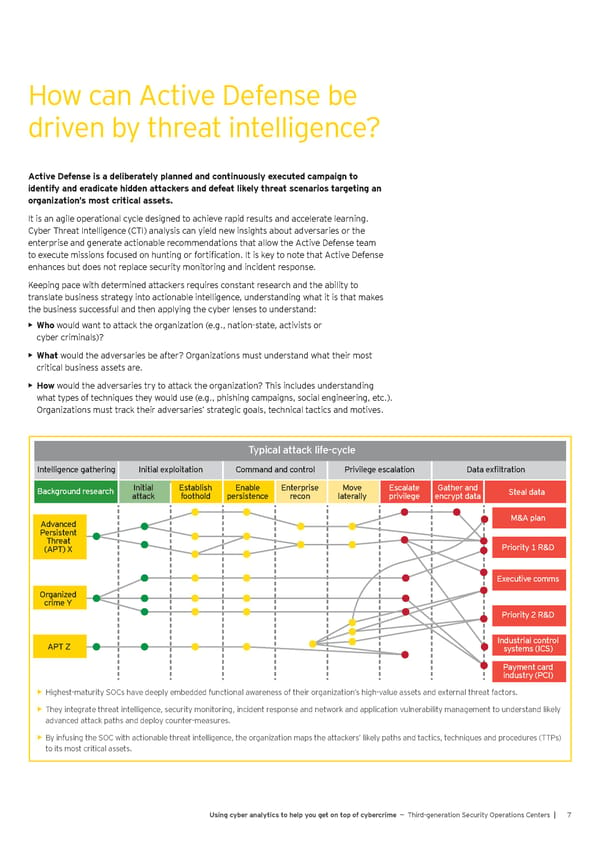
How can Active Defense be driven by threat intelligence? Active Defense is a deliberately planned and continuously executed campaign to identify and eradicate hidden attackers and defeat likely threat scenarios targeting an organization’s most critical assets. It is an agile operational cycle designed to achieve rapid results and accelerate learning. Cyber Threat Intelligence (CTI) analysis can yield new insights about adversaries or the enterprise and generate actionable recommendations that allow the Active Defense team to execute missions focused on hunting or fortification. It is key to note that Active Defense enhances but does not replace security monitoring and incident response. Keeping pace with determined attackers requires constant research and the ability to translate business strategy into actionable intelligence, understanding what it is that makes the business successful and then applying the cyber lenses to understand: • Who would want to attack the organization (e.g., nation-state, activists or cyber criminals)? • What would the adversaries be after? Organizations must understand what their most critical business assets are. • How would the adversaries try to attack the organization? This includes understanding what types of techniques they would use (e.g., phishing campaigns, social engineering, etc.). Organizations must track their adversaries’ strategic goals, technical tactics and motives. Typical attack lifecycle Typical attack life-cycle Intelligence gathering Initial exploitation Command and control Privilege escalation Data exfiltration Background research Initial Establish Enable Enterprise Move Escalate Gather and Steal data attack foothold persistence recon laterally privilege encrypt data Advanced M&A plan Persistent Threat Priority 1 R&D (APT) X Executive comms Organized crime Y Priority 2 R&D Industrial control APT Z systems (ICS) Payment card industry (PCI) Highest-maturity SOCs have deeply embedded functional awareness of their organization’s high-value assets and external threat factors. • They integrate threat intelligence, security monitoring, incident response and network and application vulnerability management to understand likely • advanced attack paths and deploy counter-measures. By infusing the SOC with actionable threat intelligence, the organization maps the attackers’ likely paths and tactics, techniques and procedures (TTPs) • to its most critical assets. Using cyber analytics to help you get on top of cybercrime — Third-generation Security Operations Centers | 7
 Using Cyber Analytics to help you get on top of Cybercrime Page 8 Page 10
Using Cyber Analytics to help you get on top of Cybercrime Page 8 Page 10