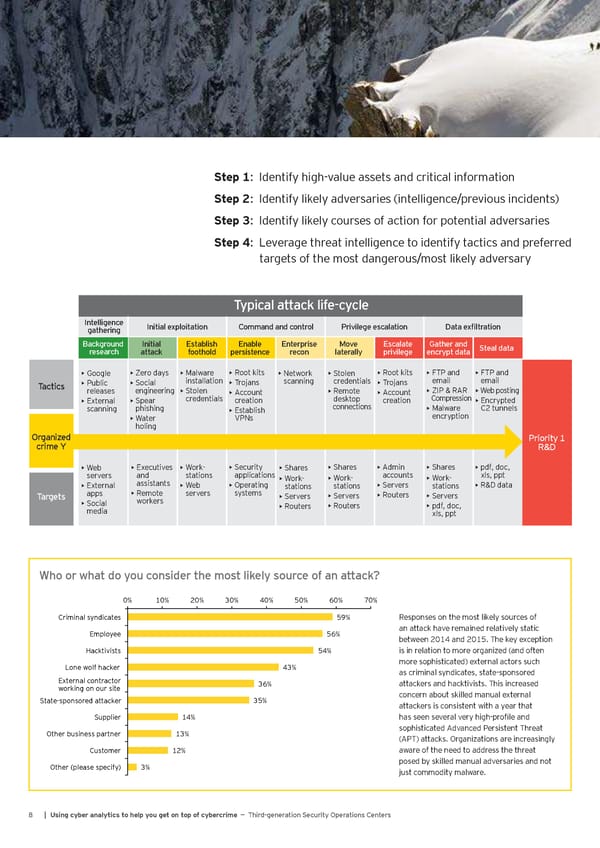
Step 1: Identify high-value assets and critical information Step 2: Identify likely adversaries (intelligence/previous incidents) Step 3: Identify likely courses of action for potential adversaries Step 4: Leverage threat intelligence to identify tactics and preferred targets of the most dangerous/most likely adversary Leverage threat intelligence to identify tactics Typical attack life-cycle Intelligence Initial exploitation Command and control Privilege escalation Data exfiltration gathering Background Initial Establish Enable Enterprise Move Escalate Gather and Steal data research attack foothold persistence recon laterally privilege encrypt data Google Zero days Malware Root kits Network Stolen Root kits FTP and FTP and • • • • • • • • • Public Social installation Trojans scanning credentials Trojans email email Tactics • • • • ZIP & RAR Web posting releases engineering Stolen Remote • • • Account • Account credentials • desktop • Compression External Spear creation creation Encrypted • • connections • scanning phishing Malware C2 tunnels Establish • • encryption Water VPNs • holing Organized Priority 1 crime Y R&D Web Executives Work- • Security Shares • Shares • Admin • Shares • pdf, doc, • • • applications • accounts xls, ppt servers and stations Work- Work- Work- External assistants Web Operating • • Servers • R&D data • • • stations stations • stations • apps Remote servers systems • Servers • Routers Servers Targets Social workers • Servers • • • Routers Routers pdf, doc, media • • • xls, ppt Who or what do you consider the most likely source of an attack? 0% 10% 20% 30% 40% 50% 60% 70% Criminal syndicates 59% Responses on the most likely sources of Employee 56% an attack have remained relatively static between 2014 and 2015. The key exception Hacktivists 54% is in relation to more organized (and often Lone wolf hacker 43% more sophisticated) external actors such as criminal syndicates, state-sponsored External contractor 36% attackers and hacktivists. This increased working on our site concern about skilled manual external State-sponsored attacker 35% attackers is consistent with a year that Supplier 14% has seen several very high-profile and Other business partner 13% sophisticated Advanced Persistent Threat (APT) attacks. Organizations are increasingly Customer 12% aware of the need to address the threat Other (please specify) 3% posed by skilled manual adversaries and not just commodity malware. 8 | Using cyber analytics to help you get on top of cybercrime — Third-generation Security Operations Centers
 Using Cyber Analytics to help you get on top of Cybercrime Page 9 Page 11
Using Cyber Analytics to help you get on top of Cybercrime Page 9 Page 11